第一部分值得学完后再回头看看,做做PPT之类的,便于记忆。
Introduction to the Penetration Tester Path
The first module is an introduction to the penetration tester path and finally get CPTS certificate. This module give some details about how to use HTB Academy, repeatly practise and assess to reinforce concepts and builds muscle memory.
An essential part of penetration test is legal and ethical, and whether our action is legitimate or not depends on one term- permission. In the learning process, we can use HTB lab or other sources. However, we have to get permission in the real world, especially the agreement with client's signature.
So, the first important rule:
[!NOTE]
there is a copy of the signed contract and a formal document listing the scope of assessment, email, phone numbers and IP range. When performing testing, stay within the scope of testing, if in doubt, ask client for addtional approvals. 第一条重要的准则就是一定要有合同的副本,以及正式文件内容包含了审查范围,比如IP,电话,邮件等等,一旦开始测试,永远在范围内行动,如果有疑问,需要联系客户获得额外的批准次啊可以
The next import thing is
[!NOTE]
document, document and document, do not fear to overcommunicate and documents. 下一个很重要的事情就是记录,详细的记录所得到的信息,并且不要害怕和客户过度沟通和记录。
如果觉得基础不够可以先看看 Information Security Foundations skill path to build prerequisite knowledge.
Academy Modules Layout
前面讲解了HTB的由来,目标等等,涉及到CPTS的部分,大致分为下面几步,
- 第一部分是Pre-Engagement, in this step, everything like the main commitments, tasks, scope, limitation,and related agreements must be documented in writing. Also, the essential imformation must be exchanged at this step, depending on the type of assessment. 预定合约阶段,基本上就是和客户进行沟通,确定目标,范围,限制等等。
- 接下来的几个部分其实是来回穿插的,包括Information Gathering, Post-Exploitation, Vulnerability Assessment, Exploitation, Lateral Movement.
- Information Gathering represents we firstly identify the overview of target system. Client may give us some details like the name of domain, the network and components of their system, a listing of their IP address. 第一次信息获取阶段就是对目标系统进行整体的一个概况描绘,可能客户会给予一些信息比如IP范围,比如域名等等,也可能什么也不给。因此,我们必须首先识别目标
这里module建议看几个模块,基本就是之前说的那个前置课程内容,大概是10天左右,可以考虑看一看。此外还加了一个modules, ***JavaScript Deobfuscation***
- 下一个部分就是Vulnerability Assessment, we can leverage the information we found to identify potential weaknesses., We also use automated tools or manually scan the target systems to looking for the vulnerability or pential vulnerability. 这里我们就是i通过刚才获取到的信息,然后使用自动化或者手动工具来扫描目标系统来寻找潜在的漏洞。
这里就是第三个rules,
> [!NOTE]
> if we pay more patience, time, and personal commitment in Information Gathering step, then we will collect enough or deep dive enough. Many penetration testers tend to jump staight into Vulnerability step without collect enought information, then they often fails and can lead to loss of time.
- After the first time of vulnerability assessment, we have to analysis the target at this step. We try to discover gaps and oppotunities to gain unintended access or privileges. Try to exploit something if there is one gap or weakness. Then, go to post-exploitation step to escalate priviledges on the target system. Or move from already exploited system to other systems through the network. Finally, returning to the information gathering to collect more. 好了,到了这一步基本就是收集信息,然后利用信息开始漏洞的查找审核,然后利用漏洞进行提权等操作,然后进一步的横向扩展移动寻找更多的目标,更多的潜在的漏洞,以及获取更多的信息。这几个步骤都是反反复复,息息相关的。
- 倒数第二个部分就是Proof of Concept or PoC. After clients receive our report, they will try to confirm the vulnerabilities found by reproducing. And costumer must carefully test issues and fix to ensure other system will not be impacted or do not have negative effect on other systems. 这个阶段就是把报告给客户后,需要重现一切漏洞或者攻击的路径,并且仔细小心的进行修复,不能对其他系统有负面影响。
- 最后一个部分就是Post-Engagement, in this stage, we have remove what have done in target systems like the bind shell, captured crendentials, etc., to prevent be exploited using by bad guys. 最后就是把自己干过的那些尾巴什么的都收拾了,不能留一堆东西被坏人利用。
# Academy Exercises & Questions
Rules第四条,
> [!NOTE]
> in the reality, we do not know how many vulerability there are and we do not always have a standard answer. So, the fourth rule is find as many vulnerabilities as possible within the given time. 这里是说在现实中,我们永远不知道到底有多少漏洞,也不是永远都有一个标准的答案,因此必须在给定的时间内找出尽可能多的漏洞。
第五个rules,
> [!NOTE]
> sometimes we may encouter difficulty tasks which maybe challenge ourself. This is very normal situation. We may stuck or frustated here, so do not shy to look for an assistance. Instead of asking " what is the answer of XXX" or " I can not solve XXX", try list what we know and what have tried for helping. 很多时候我们会遇到困难的任务,这很正常,我们可以从这里学到很多,假若我们卡在哪里,不要害羞,大胆的问,同时不要问这个的答案是什么之类的问题,而是尽量描述我们尝试了什么,得到一些线索来继续进行。
# Penetration Testing Overview
IT is very import in almost every company, attackers are increacingly attack corporate networks to damage the company, breach data to sell to competitors, etc. So, the purpose for penetration test is to simulate a real attack to determine client's IT security vulnerabilities and test their IT infrastructure. We apply various techniques to reduce the impact. 这里还是讲pentester的行为的目的和意义是啥。
All IT security teams are tend to identify, evaluate and mitigate any potential risks that could damage the CIA( confidentiality,intergrity and availability) of organizations's information systems and data.
Penetration tester are not keeping monitoring the whole period of target system, but a momentary snapshot of the security status. So pentester do not change code, or implement patches, but provide appropriate remediation recommdation to customer for eliminating risks. One more thing, it is impossible to mitigate every petential risks, but can be controlled in a accepted range.
One tips here, > [!NOTE]
> some company may use third party entities like the AWS cloud, so pentesters must gain explicit authorization in written approval from these entities.
Some cases, client may do not have experience about pentest before, so we have to explain the entire process in detail to make sure they have a clear understanding of our activities, we even need help them to scope the assessment accurately.
Due to pentester can find many personal information like names, addresses, credit card data. Accordingly, we recommend out customer to notice their employees for privay reason, and change their password as soon as possible.
Test methods includes external and internal penetration test. External represent attacking from the internet, and we have to perform our tesing via VPN or from VPS to prevent to be blocked. In some cases, client requests pentester stealthy or gradually become noisier to test their detection capabilities. Whereas, internal penetration tester means we need perform out testing from within the corporate network, or even physical presence at client's facility.
Here are types of penetration testing according to the given information
|Type |Information Provided |
|---------|---------|
|Blackbox|Minimal. Only the essential information, such as IP addresses and domains, is provided.|
|Greybox|Extended. In this case, we are provided with additional information, such as specific URLs, hostnames, subnets, and similar.|
|Whitebox|Maximum. Here everything is disclosed to us. This gives us an internal view of the entire structure, which allows us to prepare an attack using internal information. We may be given detailed configurations, admin credentials, web application source code, etc.|
|Red-Teaming|May include physical testing and social engineering, among other things. Can be combined with any of the above types.|
|Purple-Teaming|It can be combined with any of the above types. However, it focuses on working closely with the defenders.|
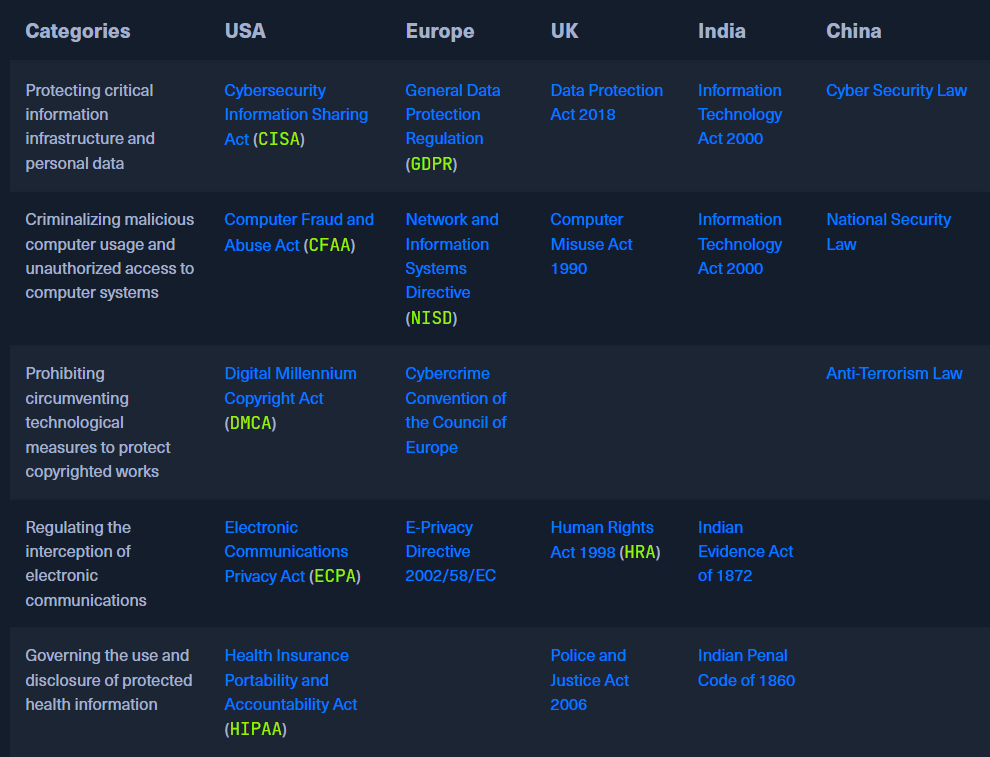
# Laws and Regulations
Each country has its own specific laws and regulations to regulate computer-related activities, copyright protection, interception of electronic communications, etc,. Pentesters must follow these laws to ensure the research activies are compliant and do not violent any provision of laws. Some instances of laws:
***CISA***: https://www.cisa.gov/resources-tools/resources/cybersecurity-information-sharing-act-2015-procedures-and-guidance
***GDPR***: https://gdpr-info.eu/
And in New Zealand, we have NZISM, CERT, etc,.
The below tips are what we can follow to avoid violating most laws:
```
Precautionary Measure
☐ Obtain written consent from the owner or authorized representative of the computer or network being tested
☐ Conduct the testing within the scope of the consent obtained only and respect any limitations specified
☐ Take measures to prevent causing damage to the systems or networks being tested
☐ Do not access, use or disclose personal data or any other information obtained during the testing without permission
☐ Do not intercept electronic communications without the consent of one of the parties to the communication
☐ Do not conduct testing on systems or networks that are covered by the Health Insurance Portability and Accountability Act (HIPAA) without proper authorization
```
# Penetration Testing Process
Again, penetration testing does not have a unchanging process, and does not represent a fixed recipe or step by step guide. Instead, a serial stages are presented a circular processes. Accordingly, the penetration testing process with its stages look as follows:
***Pro-Engagement***: In a face to face meeting or video conference call, client is educating and adjusting the contract, all necessary tests and their components are strictly defined and recorded. For instance, Non-disclosure agreement, Goals, Scope, Time estimation, Rules, etc. During this stage, many questiones are asked like what they want to be tested, and we explain in detail how to make the test as efficient as possible.
Here, the most common NDA is Bilateral NDA which means both parties are obligated to keep the resulting and acquired information confidential.
***Information Gathering***: obtain and collection necessary components the client are using and the information about the target
***Vulnerability Assessment, Exploitation, Post Exploitation, Lateral Movement, Proof of Concept, Post Engagement. All are same to above***.
***这里每一个都很详细,回过头来可以继续重新看看,做个PPT背一背***。
***Practice***
So, at last, the resommendation is learn 2 modules, and then do 3 retired machines, next try 5 active machines, finally practice 1 pro lab.
