Agenda
- Welcome
- Course Outline Review
- Context
- Security Introduction
- Forensics Introduction
- Case Study – Casey Anthony
- Paper Assessment Requirements
这节课基本是上学期的延续,但是更加侧重网络取证调查部分。
Security & Forensics
首先讲了,security和digital forensics两者的相关性,其实各自分别是一个领域,但是中间有交叉的部分。
[!NOTE]
Security come first, forensics comes after a successful attack
The pupose of security is let the 'good guy' in and keep the 'bad guy' out.
Security is an term and includes:
- Authentication
- Authorisation
- Confidentiality
- Interity
- Availability
- Non-repudiation
System generally incorporate most of these, but not always all of them
Security Triangle

[!NOTE]
We could not buy a $1000 safe to protect a $100 not, it is all about worthy.
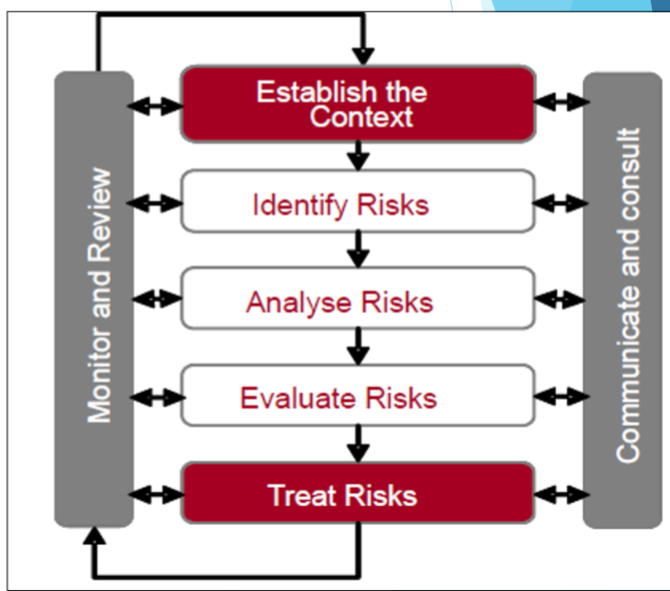
What we should do?
- Establish the context
- Identify what the risks are
- How?
- Analyse the risk
- How do we know what to analyse?
- Evalute the risk
- How do we know the system?
Prepare or Spend or Ignore
Some threat modellling
Mirrosoft STRIDE methodology
PASTA (The Procss for Attack Simulation and Threat Analysis)
Trike
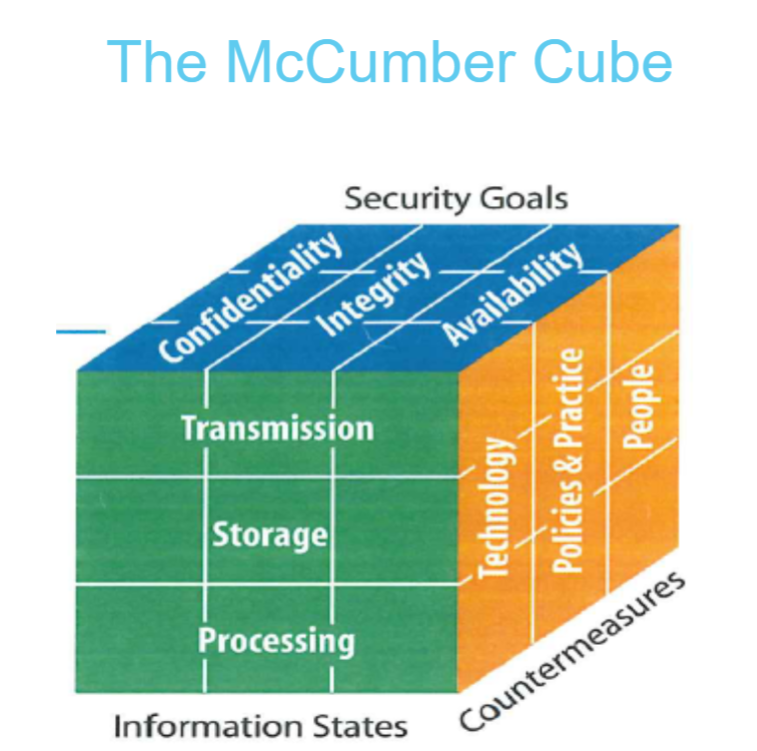
The McCumber Cube
The third dimension of the cybersecurity sorcery cube.
Only focus the countermeasures:
- Tehnologies
- Policies and Practices
- People
While Policy are not always functional. Also, it is controdictied to the convenient.
Risk Treatment
- Accesptance
- Mitigation
- Elimination
- Transference
[!NOTE]
It is impossible to build 100% security host.
Security Standards and Policy
- NIST
- ISO (Implementation of ISO 7498-2:1989 — Information processing systems — Open systems Interconnection — Basic reference model — Part 2: Security architecture)
- US National Research Council State
Network Forensics
The definition of components of Computer can be found in Crimes Amendment Act 2003 Section 249-252.
Forensics
Live Forensics: something is happening NOW, so do something: Monitor or Trace or Stop.
What we can use for network forensics?
- Log files
- Computers
- Servers
- Switches – perhaps
- Firewall
- What if we utilise Cloud services
- May I seize your Cloud Server please?
- *%$@#%
- What about personal network devices (BYOD!)
- May I take your mobile phone for investigation/copying?
- *%$@#%
Assessment
Academic Argument
Case Study Rreport
Questionnaire
LAB
The aim of this labotary exercise is to undertake a forensic examination of browser histories to become familiar with the history location, format, privacy mode in some browsers and the software that can be utilised to discover and display browser history.
Lab Software
Netanalysis
It is not free and trial version cannot be running on the virtual machine.
Lab exerciese in Firefox v 2.0
- Install an older version of firefox which was used in 2008 when Caylee Anthony case was examined.
- Turn the hided file and folders setting off in File Explorer Options - Viewe - Show hidden files, folders, and drives.
- Locate to the default firefox web data stored folder, C drive - Users - Chao - AppData - Roaming - Mozilla - Firefox - Profiles - XXX.default - history.dat
Here is default data
// <!-- <mdb:mork:z v="1.4"/> -->
< <(a=c)> // (f=iso-8859-1)
(8A=Typed)(8B=LastPageVisited)(8C=ByteOrder)
(80=ns:history:db:row:scope:history:all)
(81=ns:history:db:table:kind:history)(82=URL)(83=Referrer)
(84=LastVisitDate)(85=FirstVisitDate)(86=VisitCount)(87=Name)
(88=Hostname)(89=Hidden)>
<(80=LE)(81=http://en-us.www.mozilla.com/en-US/firefox/2.0.0.10/firstrun/)
(82=1714524988789509)(83=en-us.www.mozilla.com)(84=1)(85
=https://en-us.www.mozilla.com/en-US/firefox/2.0.0.10/firstrun)
(86=https://www.mozilla.org/en-US/firefox/2.0.0.10/firstrun)(87
=1714524992705747)(88=mozilla.org)(89
=https://www.mozilla.org/en-US/firefox/2.0.0.10/firstrun/)(8A
=https://www.mozilla.org/en-US/firefox/new/?reason=outdated)(8B
=G$00e$00t$00 $00F$00i$00r$00e$00f$00o$00x$00 $00f$00o$00r$00 $00d$00e$00s\
$00k$00t$00o$00p$00 $00$14 $00M$00o$00z$00i$00l$00l$00a$00 $00($00U$00S$00\)$00)>
{1:^80 {(k^81:c)(s=9)[1(^8C=LE)]}
[2(^82^81)(^84^82)(^85^82)(^88^83)(^89=1)]
[3(^82^85)(^84^82)(^85^82)(^88^83)(^89=1)]
[4(^82^86)(^84^87)(^85^87)(^88^88)(^89=1)]
[5(^82^89)(^84^87)(^85^87)(^88^88)(^89=1)]
[6(^82^8A)(^84^87)(^85^87)(^88^88)(^87^8B)]}
@$${2{@
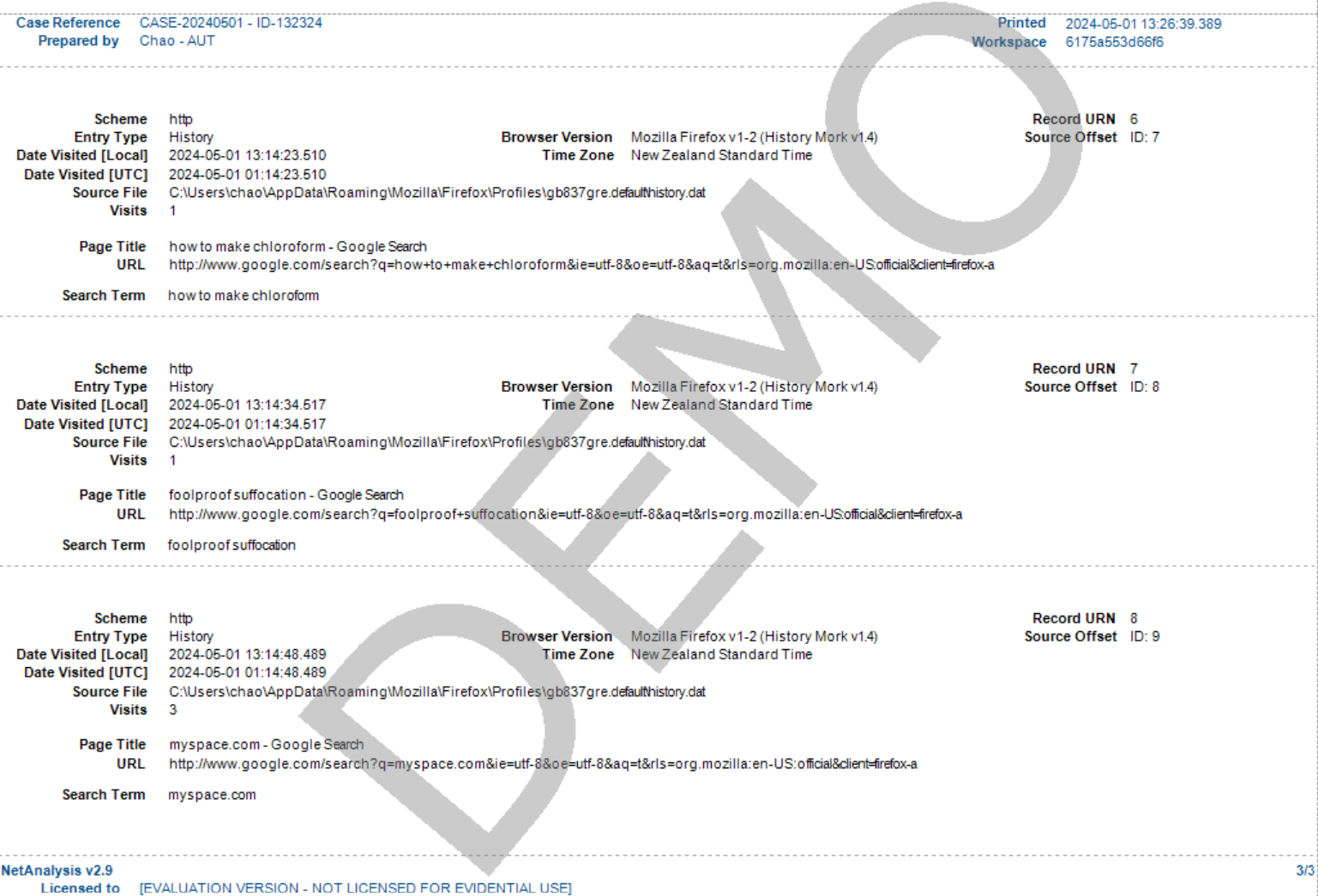
@$$}2}@- Then do some search in the browser: How to make chloroform, foolproof suffocation, myspace.com (three times).
- Now, the history.dat is updated to below:
// <!-- <mdb:mork:z v="1.4"/> -->
< <(a=c)> // (f=iso-8859-1)
(8A=Typed)(8B=LastPageVisited)(8C=ByteOrder)
(80=ns:history:db:row:scope:history:all)
(81=ns:history:db:table:kind:history)(82=URL)(83=Referrer)
(84=LastVisitDate)(85=FirstVisitDate)(86=VisitCount)(87=Name)
(88=Hostname)(89=Hidden)>
<(80=LE)(81=http://en-us.www.mozilla.com/en-US/firefox/2.0.0.10/firstrun/)
(82=1714524988789509)(83=en-us.www.mozilla.com)(84=1)(85
=https://en-us.www.mozilla.com/en-US/firefox/2.0.0.10/firstrun)
(86=https://www.mozilla.org/en-US/firefox/2.0.0.10/firstrun)(87
=1714524992705747)(88=mozilla.org)(89
=https://www.mozilla.org/en-US/firefox/2.0.0.10/firstrun/)(8A
=https://www.mozilla.org/en-US/firefox/new/?reason=outdated)(8B
=G$00e$00t$00 $00F$00i$00r$00e$00f$00o$00x$00 $00f$00o$00r$00 $00d$00e$00s\
$00k$00t$00o$00p$00 $00$14 $00M$00o$00z$00i$00l$00l$00a$00 $00($00U$00S$00\)$00)>
{1:^80 {(k^81:c)(s=9)[1(^8C=LE)]}
[2(^82^81)(^84^82)(^85^82)(^88^83)(^89=1)]
[3(^82^85)(^84^82)(^85^82)(^88^83)(^89=1)]
[4(^82^86)(^84^87)(^85^87)(^88^88)(^89=1)]
[5(^82^89)(^84^87)(^85^87)(^88^88)(^89=1)]
[6(^82^8A)(^84^87)(^85^87)(^88^88)(^87^8B)]}
@$${2{@
@$$}2}@
@$${4{@
<(8C
=http://www.google.com/search?q=how+to+make+chloroform&ie=utf-8&oe=utf-8&a\
q=t&rls=org.mozilla:en-US:official&client=firefox-a)(8D=1714526063510610)
(8E=google.com)(8F
=h$00o$00w$00 $00t$00o$00 $00m$00a$00k$00e$00 $00c$00h$00l$00o$00r$00o$00f\
$00o$00r$00m$00 $00-$00 $00G$00o$00o$00g$00l$00e$00 $00S$00e$00a$00r$00c$00h$00)>
{1:^80 {(k^81:c)(s=9)1 } [-7(^82^8C)(^84^8D)(^85^8D)(^88^8E)(^87^8F)]}
@$$}4}@
@$${5{@
<(90
=http://www.google.com/search?q=foolproof+suffocation&ie=utf-8&oe=utf-8&aq\
=t&rls=org.mozilla:en-US:official&client=firefox-a)(91=1714526074517599)
(92
=f$00o$00o$00l$00p$00r$00o$00o$00f$00 $00s$00u$00f$00f$00o$00c$00a$00t$00i\
$00o$00n$00 $00-$00 $00G$00o$00o$00g$00l$00e$00 $00S$00e$00a$00r$00c$00h$00)
(93
=http://www.google.com/search?q=myspace.com&ie=utf-8&oe=utf-8&aq=t&rls=org\
.mozilla:en-US:official&client=firefox-a)(96=1714526088489811)(94
=1714526081038381)(95
=m$00y$00s$00p$00a$00c$00e$00.$00c$00o$00m$00 $00-$00 $00G$00o$00o$00g$00l\
$00e$00 $00S$00e$00a$00r$00c$00h$00)(98=3)>
{-1:^80 {(k^81:c)(s=9)1 } 2 3 4 5 6 7 [-8(^82^90)(^84^91)(^85^91)(^88^8E)
(^87^92)]
[-9(^82^93)(^84^96)(^85^94)(^88^8E)(^87^95)(^86=3)]}
@$$}5}@- We can find some information here, but it is not easy to read. Let us use Netanalysis. We can see very detailed information includes Local time, UTC time, search times, etc.
- If I manually changed some data in history,dat, NetAnalysis will get the changed data as well instead of the original data. Also, if we clear the cache in Tools - Clear Private Dta - Clear Private Data Now. The data will not exist any more in either history.data or Netanalysis.
// <!-- <mdb:mork:z v="1.4"/> -->
< <(a=c)> // (f=iso-8859-1)
(8A=Typed)(8B=LastPageVisited)(8C=ByteOrder)
(80=ns:history:db:row:scope:history:all)
(81=ns:history:db:table:kind:history)(82=URL)(83=Referrer)
(84=LastVisitDate)(85=FirstVisitDate)(86=VisitCount)(87=Name)
(88=Hostname)(89=Hidden)>
<(80=LE)>
{1:^80 {(k^81:c)(s=9)[1(^8C=LE)]} }
[3:^80]
[4:^80]
[5:^80]
[6:^80]
[7:^80]
[8:^80]
[9:^80]
[2:^80]
@$${8{@
@$$}8}@
@$${9{@
@$$}9}@Lab exerciese in Firefox (latest version)
- Install the latest version of firefox.
- Locate to the default firefox web data stored folder, C drive - Users - Chao - AppData - Roaming - Mozilla - Firefox - Profiles - XXX.default. For the new firefox, the history data will be stored in a variety of files that is difficult to read. So, we still use NetAnalysis to read. Here we can see lots of information includes cookie, tab history, etc.
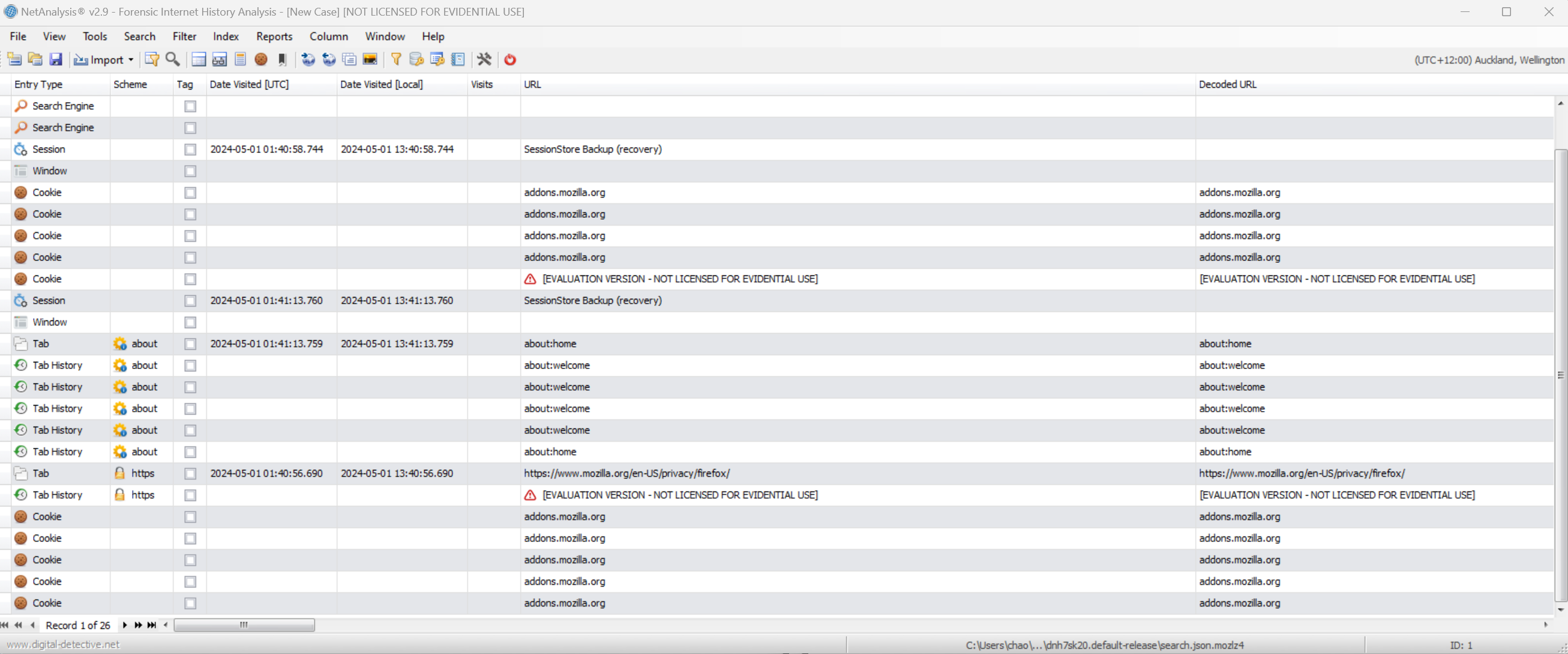
- Now, let's search something: How to make chloroform, foolproof suffocation, myspace.com (three times).
- Now, the history.dat is updated to below:
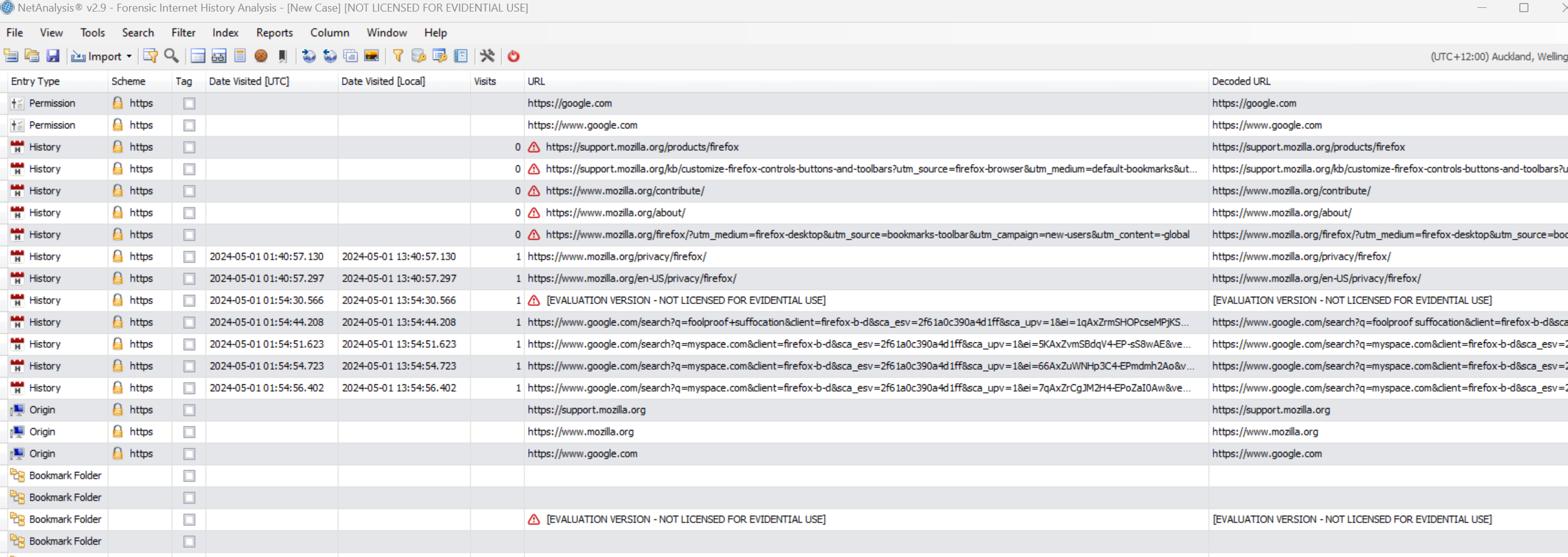
-
Another path: If we type about:cache in the search bar, we also can get some information here.
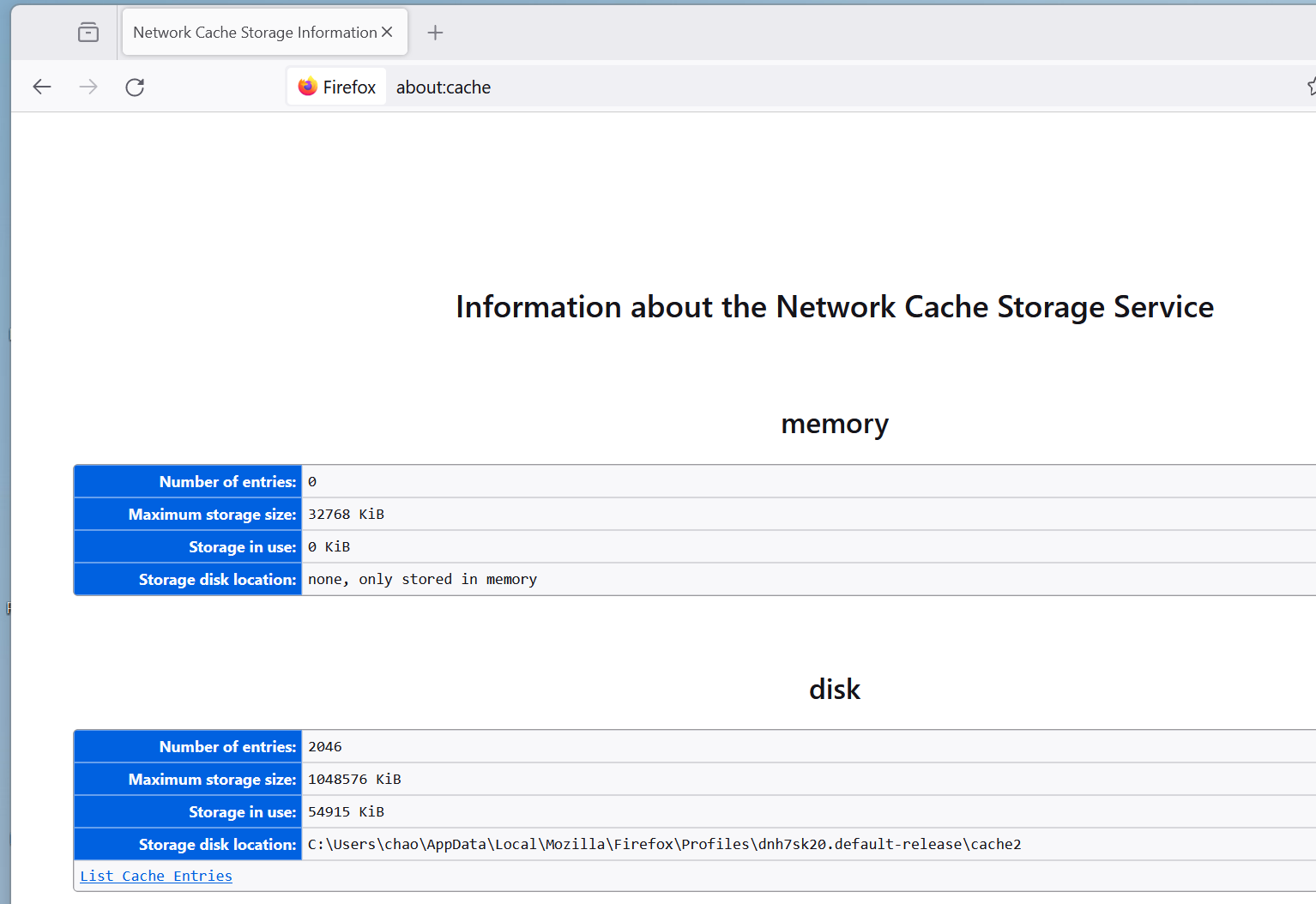
-
In the middle entry ‘disk’, there is
some information about what has been stored on the hard drive disk. Under ‘Storage disk location’
there is the pathway C:\Users\Lecturer\AppData\Local\Mozilla\Firefox\Profiles\a69e1ba4.default-release\cache2
We can also do some testing in IE, Chrome, etc.
