考试的表现可以说堪称灾难,时间不足,难度很高,一上来就慌了,有几个很简单的题没做,而且浪费了时间,后面难的题没时间思考。
终于,老师讲了一下答案。
第一道题我一开始找到了三个点,所以以为三个点就对,实际上,一个点价值0.5,六个点才对。

Answer: List anomalies:
1。sdb 但是后面成了sdc

2。没有sha1

3。hash应该是log,命令错误
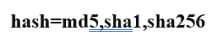
4.计算一下大小就知道157444太大了,一个sector 才512 bytes,所以15744才对

5。这里 应该分是分开的, log=md5 log=sha256

6.十六进制不应该有g

第二道题我慌了,其实这个反而很简单

2a: Explain which of the 5 files this is the start of. You must explain how you know which it is.
Answer: 00000128.jpg, 0x10000转成十进制是65536,除以512byte 刚好是第128sector
2b: Use this screenshot to calculate how many sectors the drive is. You must show the calculation based on the screenshot above:
Answer: 0x7B0000转成十进制是8060928,除以512byte 刚好是15744

3a: The expert states that this NTFS drive is formatted with a cluster size of 2048 kilobytes. How many clusters will this file be allocated on the drive?
Show the calculation:
Answer:
1 clusters
2048 kilobytes = 2,048,000 more than 656,253. So, this file only use 1 cluster
3b: Show with a calculation that 8,060,928 bytes is 7.6875 MiB
Answer:
8.060,928 bytes/ 1024 = 7, 872 KiB 7,872 KiB / 1024 = 7.6875 MiB


And then recover the files with Foremost:

The expert then used hexedit to show the start and end of the file:


Start file signature =? FF D8 FF E0
End file signature = ? FF D9
4a: Calculate the size of the file from the screenshots and state, with proof, whether you agree that the demonstration has shown the correct file size or not:
Answer:
21FD5 in Hex = 139221 in Dec; 1B800 in Hex = 112640 in Dec; the files size= 139221-112640=26581 bytes. So, I agree the size is correct
The expert then states that there is slack space after the end signature that could fit a small file. Show, with calculation, the size of the slack space in bytes
(note: ignore that it is bigger than a single cluster):
Answer:
28672-26531=2091 bytes 这里是需要看windows界面,占用大小和实际大小减去即可
What type of slack space is this called (0.5 marks)?
Answer: Drive Slack Space
What anomaly do you see that leads you to question the evidence recovered (0.5 marks)?
Answer:
dd command cannot use “hash=md5”, this is anomaly.
5: Briefly discuss why Open Source Tools, such as those available in Linux, may comply better with the Daubert Principles than commercial tools such as Encase and FTK. Be specific with your reasons. Vague or general statements will gain little or no marks. Support your discussion with the reading(s) from class.(2 marks)
Guide: 100 words
Answer:
这道题就是我没有看阅读材料,不然肯定明白,error rates 以及peer review of code
6: A forensic investigator images an SSD drive and receives calculates an MD5 hash. 25 deleted files are then recovered from the drive. A second investigator follows the same procedure and recovers the same deleted files, but a different md5 hash value is calculated. The hash values are verified as correct. Explain what has likely occurred.(1 mark)
Answer:
很多人包括我都写的是GC,但是假如发生了GC那么恢复的文件就应该不一样,所以这里是wear levelling



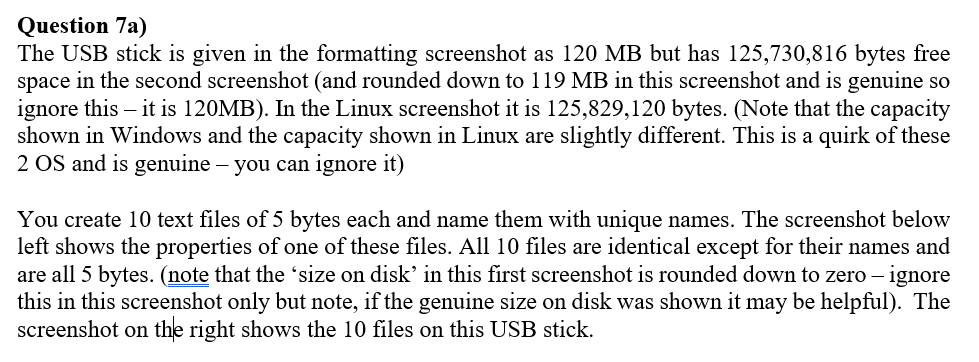


Formatting the drive used 49,152 bytes of space on the drive. (screenshot 2 in question 7). The 10 files were 5 bytes each so a total of 50 bytes. This should use 49,152 plus 50 bytes for a total of 49,202 bytes – shouldn’t it?
Explain and include a calculation showing why 212,992 bytes is used (‘used space’ in final screenshot) on the USB stick and not 49,202 bytes.
Answer:
这里,原始49152没问题,然后10个分件要看每个占用的sector是多少,我看的是linux显示512当然不对,应该看windows里 一个占用16kib,因此16kib * 10 +49152 = 212992
Question 8:
What type of hash is this and explain how you know this?(0.5 marks)
63e6d862b4e2c005ab9efc6104cea7bef4f5e1a7
Answer:
This is SHA1, because it has 40 hexadecimal, while MD5 is 32 and SHA256 is 64
Question 9:
You are acting with a search warrant to seize computers that belong to an organisation. You obtain evidence from a computer used by an employee in that organisation. At the time you assumed it was an organisation-issued computer belonging to the company. You find evidence of a crime. You then discover that this computer is the personal computer belonging to the employee and is not covered under the search warrant. Briefly discuss whether the evidence found will still be available to prove the crime in court. Include the term related to evidence (the tree metaphor) that is obtained in these circumstances:(1.5 marks)
Answer:
The answer is no, if evidence is not seized lawfully, the evidence may be excluded from court and all evidence flowing from this may also be excluded which is called fruit of the poison tree.
In some exceptional circumstances, the evidence may still be permitted but obviously this doesn’t apply in this case.
Question 10:
In a different case, you are asked to review a forensic investigator’s evidence and provide a list of any differences between what the investigator stated they did and what the evidence shows or a conflict in evidence in the various screenshots.
The investigator states that they utilised a computer that boots only to Linux so that the processing was quick. They state that they imaged a 120MiB USB stick that was formatted with FAT using the dcfldd command and recovered five deleted files using Autopsy in Linux and saved the files to a folder called evidence_files. The following screen shots are provided.
After the screenshots, list the anomalies you find. 0.5 marks for a correct anomaly, 0.5 marks deducted for an incorrectly identified anomaly. (4 marks)







Answer - List of anomalies:
- kali is used in virtualbox
- File location should be “/root/Desktop/usb.dd”
- dcfldd input file is not correct, should be “if=/dev/sdb”
- File size is wrong, should be 125,829,120 bytes not 1,000,000 bytes
- md5 hash would appear on screen
- NTFS but stated FAT
- Files not deleted(red)
- stated 5 files but 6
- dog has changed to frog
这个考卷得了11分,其实如果不慌张的话我觉得13-15我还是有希望的,还是知识掌握的不扎实。